A vulnerability in the AIX systems, published for the first time by the Bulgarian IT expert, Georgi Guninski, is part of the arsenal of the hackers of the Central Intelligence Agency (CIA) of the United States. This transpires from documents published by Wikileaks, revealing how the CIA uses a wide range of malicious software to obtain information on people of interest. The available documents do not reveal whether the spies have used this particular flaw in covert operations.
Aside Guninski, Bulgaria and Bulgarians are hardly present in the CIA documents published by Wikileaks under the codename Vault 7. There is information on several DNS resolvers with free access that are located in Bulgaria, and so far that is everything.
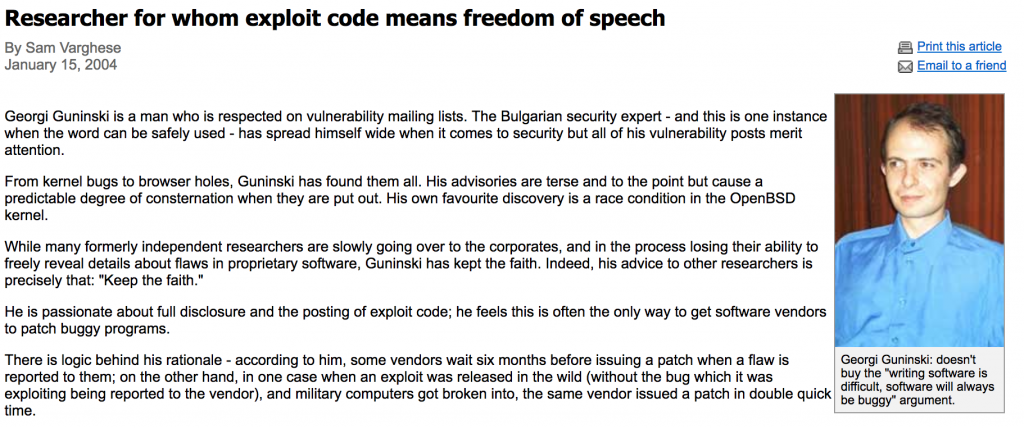
Georgi Guninski was born in 1972 and studied finances in the Sofia University for National and World Economy, but later became involved with computer security. He gained worldwide fame as a “white hacker”, finding and publishing information on dozens of critical vulnerabilities in various operating systems and browsers. In 2004, he was included in a ranking of the best computer security experts, along with Phil Zimmerman, Bruce Schneier and other global top names.
Besides publicity, which he claims he is not seeking, Guninski has earned powerful enemies such as large software companies, led by Microsoft. They accuse him of sabotaging computer security with his publications. “Buggy software is out there and killing the messenger does not help anyone. Truth is, some companies and their puppies does not like me and they use false arguments to discredit me,” is his reply.
The vulnerability in the AIX, discovered by the Bulgarian, is particularly valuable because, for a long time, this operating system was considered foolproof. Guninski, however, has accepted the challenge, has found a bug, has published it and then lost his job. Subsequently, he found many bugs in Windows and Internet Explorer over which he was threatened by Microsoft.
Georgi Guninski is no longer active in the field of computer security and has turned his attention to specialized mathematical problem solving. This is evident from his academic publications in the field of applied mathematics.
Bivol sent an email to the computer wiz with a request for comment. “The writing of this shellcode is apprentice work,” is how he downplays the importance of his discoveries. “The CIA almost certainly can write it themselves or buy another,” Guninski believes. And he is most probably right, given the scale of the cyber operations deployed by the special unit created at the CIA as a parallel structure of the National Security Agency (NSA). Documents from #Vault7 reveal that US government hackers have managed to install the ears and the eyes of the
CIA in your TV and even in your car
The archive, which, in the words of Julian Assange, is the largest collection of files leaked from the CIA, contains information about hundreds of hacking tools for breaking into networks, computers, phones and even smart TVs. They are from the period 2013 – 2016, and Wikileaks claims that only part of them has been published to date.
The unpublished zero day exploits that are not known to the manufacturers of smart devices, but are used by spies, and possibly by hackers for less noble and human rights protection goals, are particularly insidious. Infected with such a code, the device misleads its owner that is turned off while it transmits everything it “hears” with the microphone and everything it “sees” with its camera.
Much more worrying is the evidence that the CIA can hack and control the software of modern smart cars and trucks. Conspiracy theories are already spreading on Twitter, claiming that the fatal crash of Forbes journalist Michael Hastings may have been caused deliberately because of his investigations related to the spying.
Unlike the methods of the NSA, which were exposed by whistleblower Edward Snowden, CIA hackers pay less attention to strategic mass eavesdropping. They emphasize on tools for tracking an individual and obtaining information from the electronic devices they use.
According to Wikileaks, the CIA toolkit poses a great danger because a significant portion of it has not been classified as secret information and has circulated among private companies and hackers. No doubt, the publication will cause shockwaves not only in spy circles but also among device and software manufacturers. They will need to urgently plug the loopholes revealed by the documents in order to prevent the loss of consumer confidence.
“If you are taking paranoia meds because you think the government is watching you all the time you can stop taking those meds now. #Vault7,” this is how famous hacktivist and pirate Kim Dotcom summed up the significance of the #Vault7 revelations for ordinary citizens.
***
If you find this article useful, support our work with a small donation.
Pay a Bivol Tax!
We will highly appreciate if you decide to support us with monthly donations keeping the option Monthly
The form is not published.
IBAN: BG27 ESPY 4004 0065 0626 02
BIC: ESPYBGS1
Титуляр/Account Holder: Bivol EOOD
При проблеми пишете на support [at] bivol [dot] bg
This post is also available in: Bulgarian








You must be logged in to post a comment.