The attacks by the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU) on targets in the United States, France, Ukraine, and South Korea had been undertaken through servers rented out by a Bulgarian company with a Ukrainian owner. The attackers had taken advantage of the opportunity to rent the servers anonymously and without traceability. A Bivol reporter also managed to rent such a server by registering with a fake ID and paying with bitcoins. We were able to contact the Ukrainian owner, who stated that he was ready to cooperate with any investigation into the attacks. So far, however, no one is looking for him because the Bulgarian intelligence is not interested in these findings.
Information that Russian attackers had used Bulgarian servers appeared as early as mid-November 2019, in an article by respected American journalist Andy Greenberg for Wired magazine. Cybersecurity experts from the firm FireEye had identified IPs used in phishing attacks against the US Democratic Party (DCLeaks), the party of French President Macron (Macronleaks), the Pyeongchang Olympics, the Ukrainian electric power distribution grid and the NotPetya virus, inflicting USD 10 billion in damage.
Everywhere, experts have discovered the fingerprints of a cyberwar squad inside the GRU, known as the Sandworm of GRU’s unit 74455. The special counsel Robert Mueller’s investigation into Russian interference in the 2016 US election identified it as well. It indicted 12 Russian military intelligence officers for penetrating the Democratic National Convention (DNC) servers and leaking correspondence to influence the election.
Bivol examined the IPs identified by FireEye in the various attacks and found that four of them lead to servers hosted by the Bulgarian company HZ Hosting Ltd. – 185.80.53.22, 5.149.248.67, 5.149.249.172, 5.149.254.114, which is registered in Bulgaria’s second-largest city of Plovdiv.
Phantom firm bought through the Bulgarian Embassy in Kyiv
HZ Hosting Ltd. is the trademark behind the HostZealot hosting provider that offers internet servers for rent. One of our reporters visited the address of the company in Plovdiv, at 2 “Lyuben Karavelov” Street floor 3 office 5, where he found only the office of lawyer Alexander Filev and of an accounting firm.
The company has existed since 2015 when Plovdiv-based lawyer Filev has registered it under the name “Global Industrial Company” with owner and manager Vilko Lyubenov Damyanov.
Research shows that Damyanov is the listed owner of several similar companies, registered at 23 A “San Stefano” Street in the capital Sofia or at 2 “Lyuben Karavelov” Street in Plovdiv. What the companies have in common is that they have been subsequently sold to foreigners.
The same thing happened with “Global Industrial Company” just a month after it had been created. The owner of the company is Danil Eremka from Ukraine, represented by lawyer Filev with a power of attorney issued by the Bulgarian Embassy in Kiev.
Actually, Eremka has not set foot in Bulgaria to acquire and launch the business through this company. The Plovdiv bookkeeping company “Capital 2011”, which he has never visited either, does its accounting, our reporter found. HZ Hosting is serviced entirely remotely, via email.
Renting a server anonymously
Despite the above, the operations of HZ Hosting are real. The company generates turnover and posts net sales revenues (BGN 1.3 million in 2018), according to the most recent annual financial statements. The hostzealot.com site allows customers to order a server and pay with any of the popular cryptocurrencies without leaving a trace leading back to them.
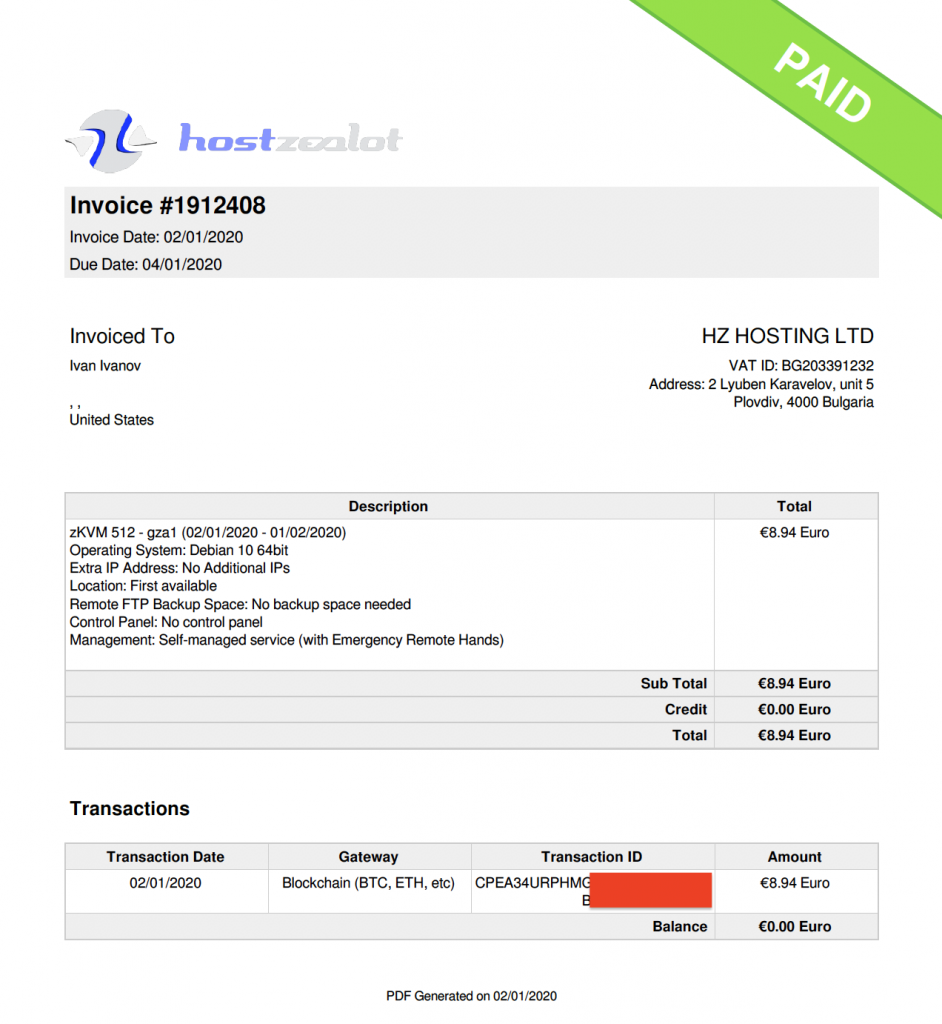
Bivol reporters checked its services by registering an anonymous email address at tutanota.com, accessing it through a VPN to mask the original IP address. Then, with that email address and the fake ID of some Ivan Ivanov from the United States ordered a server at hostzealot.com and paid for it with bitcoins.
The Bulgarian company issued an invoice for the bitcoin-paid server and should account for it accordingly. However, the customer can actually be a fake and there is no way to identify them.
The whole process of registering and paying for the server went smoothly and for a few days, the server in question had a Linux installation with a web server showing the text “This server was paid anonymously with bitcoins for the needs of a journalistic investigation by Bivol.bg“.
This proves that anyone, including a Russian GRU cyberattacker, can buy a web resource from Bulgaria in minutes without leaving a trace and then attack the target from it.
Eremka will assist the authorities if they approach him
With the help of Ukrainian colleagues of YouControl, Bivol found detailed information about the owner of HZ Hosting and hostzealot.com. The Ukrainian citizen Danilo Eremka turned out to be a real person living in Kharkiv.
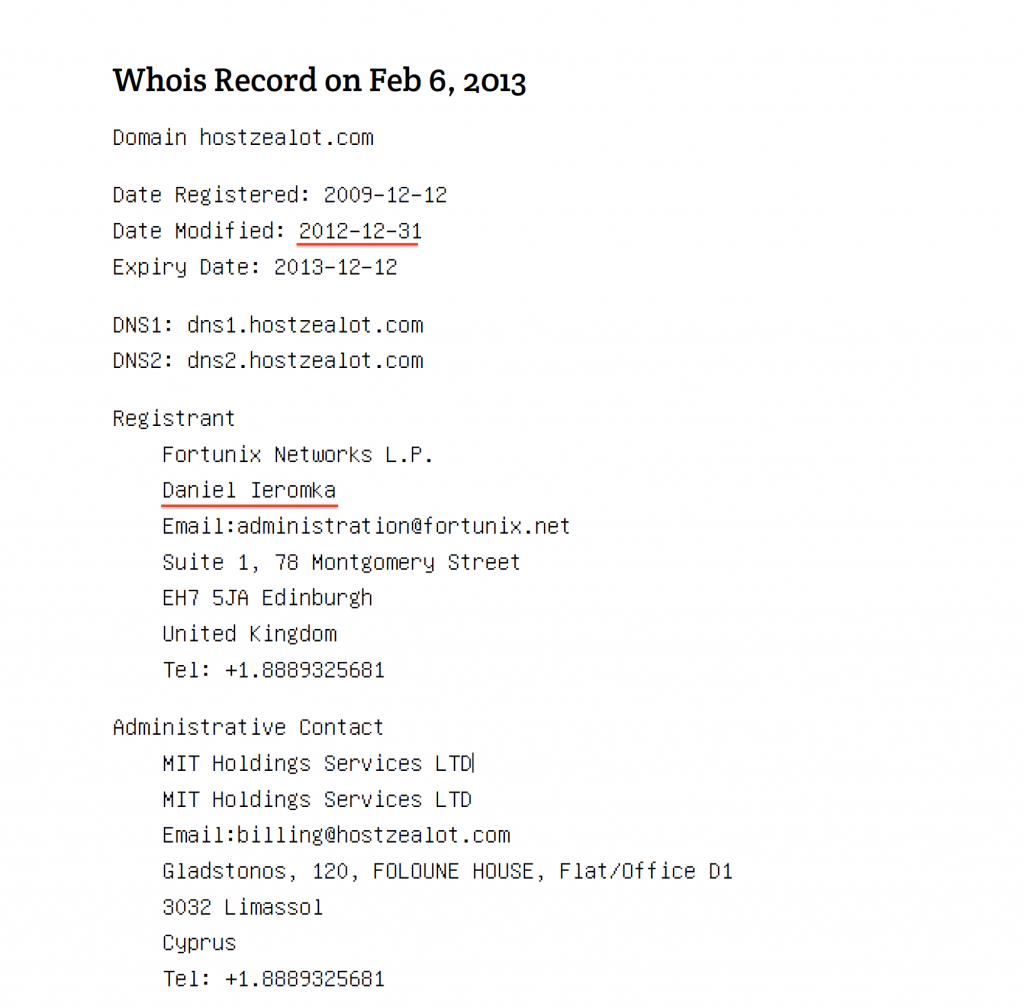
Eremka (spelled ЄРЬОМКА-YERIOMKA) is an IT specialist who, however, does not do business in his native Ukraine. There, he is only listed as the founder of the local Tesla football club. In 2012, he started a business providing Internet services with Fortunix Networks L.P., a UK-based company. At the end of 2012, he purchased the domain hostzealot.com on behalf of this company.

Danil Eremka, Photo LinkedIn https://www.linkedin.com/in/dan-ieromka-42171425/
Fortunix Networx L.P. has not lasted long in the United Kingdom, but its name is still associated with IPs that HZ Hosting currently owns.
Bivol reached Danil Eremka, who explained that he had moved his business to Bulgaria because he did not want to use offshore registration. He also had difficulty opening a bank account in the United Kingdom with Fortunix Networx L.P..
Asked for comment on the fact that Russian attackers prefer the servers he rents, Eremka said his company does not monitor what customers are doing. However, he is ready to assist the authorities if they approach him.
Nevertheless, his assistance may end up being useless because of the anonymity of the whole process of renting and paying for the servers. Danil Eremka commented that his company does risk analyses, but it was not possible to identify all risk clients. He acknowledged that cryptocurrency server shopping is particularly problematic and promised to introduce additional controls to identify customers.
From Bangladesh to Yambol
However, the Bulgarian trail in the actions of the Russian attackers does not end with the Plovdiv company HZ Hosting. Two more IPs used by them – 130.185.250.77 and 130.185.250.171 – belong to BeeHosted – Internet Services & Hosting Provider from Bangladesh, but according to the site IPINFO.io they are located in the southern Bulgarian city of Yambol.
Another IP address localization service associates these addresses with the Bulgarian company Lir.bg. Experts interviewed by Bivol commented that it was probably an old registration of the entire address network, which is currently linked to the Dutch company Global Layer BV, also mentioned in the FireEye research.
While investigating the NotPetya virus that attacked Ukraine, ESET’s cybersecurity experts have also detected the 130.185.250.171 address. The transfinance.com [.] Ua domain, used to spread the virus, as well as a Tor server command and control program named severalwdadwajunior have been registered at this address.
Even if this connection with Bulgaria turns out accidental, it still deserves a detailed probe by the Bulgarian intelligence as the use of our country as a platform for global Russian intelligence hybrid war operations is disturbing.
Bivol asked questions to the Bulgarian National Security Agency (DANS) and the government’s press office about the revelations that the GRU had used Bulgaria-related resources for its attacks, but did not receive an answer. A source from the Interior Ministry, dealing with cybersecurity, told us that there had been no research so far into the specific IPs revealed by experts.
Atanas Tchobanov and Dimitar Stoyanov worked on this story
***
If you find this article useful, support our work with a small donation.
Pay a Bivol Tax!
We will highly appreciate if you decide to support us with monthly donations keeping the option Monthly
The form is not published.
IBAN: BG27 ESPY 4004 0065 0626 02
BIC: ESPYBGS1
Титуляр/Account Holder: Bivol EOOD
При проблеми пишете на support [at] bivol [dot] bg









You must be logged in to post a comment.